Tech Data Corp. has rolled out a set of new RECON-branded security services, turning the RECON security operations center it introduced earlier into the first member of what’s now called the RECON Security Suite.
The new members of that suite, which are all available immediately in the U.S. and Canada, are billed through monthly or annual subscriptions and designed to fill niches not covered by leading names on the distributor’s line card, according to Alex Ryals, Clearwater, Fla.-based Tech Data’s vice president of security solutions for the Americas.
“The goal is absolutely not to compete with the Fortinets and the Check Points and the big vendors,” he says. Ryals spoke with ChannelPro at Tech Data’s 2018 Channel Link conference, which concludes today in Austin, Texas.
Most of the new RECON services are delivered in partnership with smaller, lesser known security software makers Ryals has come across that he feels have untapped potential.
“We’re able to leverage our brand to bring awareness to the channel for companies that I think are going to grow in the next couple years,” he says.
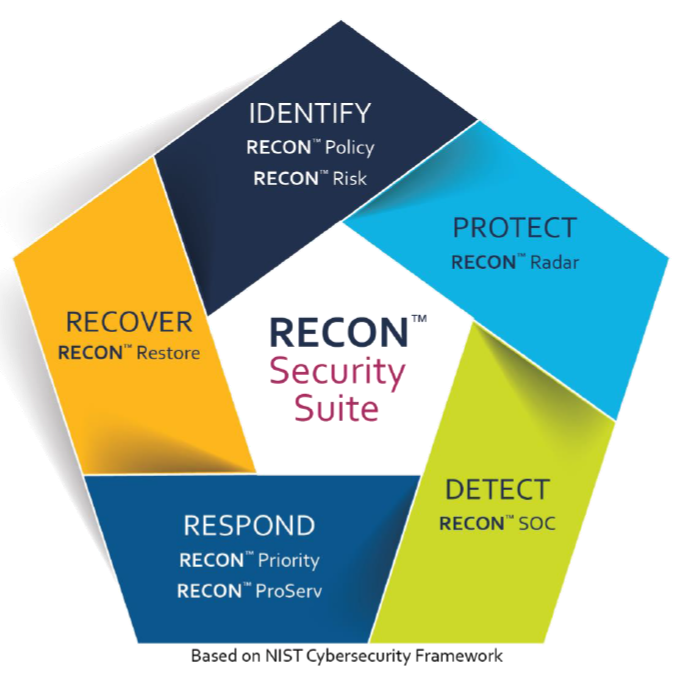
There are six new RECON services in all. Based on technology from Security Colony, of San Francisco, RECON Policy gives resellers access to a library of over 200 pre-written and vetted security policy documents.
RECON Radar, which is powered by software from Pwnie Express, of Boston, monitors all of the sometimes hard to track Bluetooth and wireless devices on a customer’s network, including Internet of Things hardware. “Whenever you have a rogue device pop on the network, they can notify you immediately,” Ryals says.
RECON Priority, which utilizes a solution called Cyr3con, from Phoenix-based Cyber Reconnaissance Inc., helps businesses determine which systems they should train their patching attention on first. The service sets bots loose in the “dark web” to see which vulnerabilities are being actively exploited by hackers. “Turns out that less than 10 percent of all vulnerabilities have an actual exploit for them, but which 10 percent?” Ryals says.
RECON Risk employs technology from Arx Nimbus LLC, of Chicago to quantify the potential financial impact of a breach. That’s information channel pros and their customers can use to cost-justify security investments and decide how much cyber-insurance coverage to buy. “It’s a pretty cool, very robust, reporting engine written by mathematicians and insurance actuaries,” Ryals says.
RECON Restore uses BDR software to either recover infected files in real time during an attack or restore compromised files after an attack. The service utilizes backup solutions from multiple vendors, including Veritas Technologies, Veeam, and Kaseya Ltd.‘s Unitrends division, according to Tracy Holtz, director of security and information management at Tech Data.
“If there’s a preference from a customer’s perspective, or an end customer, then certainly we want to lead with that brand,” she says. “If there’s not, then we look around at what their challenge currently is and what the right solution is that fits them.”
RECON ProServ, finally, offers a variety of professional and managed security services. Billed hourly and subcontracted through Tech Data resellers, those services are performed either by Tech Data’s own employees or by pre-approved, services-only partners with specialized expertise in areas like PCI-DSS compliance and virtual CISO consulting.
Collectively, Ryals says, the six new RECON services cover all five sections of the National Institute of Standards and Technology (NIST) cybersecurity framework. RECON Policy and Risk, for example, fit in the “Identify” part of the framework, RECON Radar sits in the “Protect” part, RECON Priority and ProServ reside in the “Respond” part, and RECON Restore corresponds to the “Recover” part. The previously introduced RECON SOC service, meanwhile, covers the “Detect” section of NIST’s framework.
Offering comprehensive security services for every dimension of the security challenge is essential, Ryals argues, in an age of sophisticated and ever-changing threats.
“It’s not enough to be good at firewalls anymore. It’s not enough to be good at endpoint anymore,” he says. “You have to be thinking about all the areas of security.”
From Tech Data’s perspective, offering security services based on products from up-and-coming vendors benefits everyone involved.
“I want to, number one, give smaller vendors a voice and a large distributor,” Ryals says. “Number two, I want to give my partners access to some up and coming tech that I think is unique and interesting that the big guys aren’t quite doing yet.”
Less established vendors tend to charge less than their name-brand peers, he continues, making them a good fit for SMBs in particular.
According to Holtz, Tech Data has worked extensively with all of the new RECON vendors to ensure they have the skills and scale to support large numbers of customers.
“Quite a bit of the onboarding process, as we’ve brought the vendors forward within our line card, was really helping them though our consultation approach with channel strategy,” she says. “We’ve continued to coach and direct them in the right ways around supporting the customers.”
Ryals, who is continually on the lookout for new and relatively unknown security vendors, meets with roughly three of them a week. He also visits Silicon Valley twice a year to attend “Shark Tank”-like session hosted by venture capital firms.
“Those [vendors] are too early for distribution 95 percent of the time, but it lets me see what’s coming down the pipe and what the VCs find interesting, and it lets me have an opportunity to educate some of these startups on the value of distribution to help them scale and grow a channel,” Ryals says.
Tech Data has two more RECON security services coming within the next few months, and will continue adding RECON products at the rate of two to three per quarter in the future. The company also hopes to list RECON services eventually on its StreamOne cloud computing marketplace.
Introduced in November 2016, RECON SOC provides 24×7 monitoring and management via a virtual security operations center operated by CYBERShark, a division of Piscataway, N.J.-based BlackStratus. According to Ryals, the service has been popular among smaller businesses without extensive in-house IT operations.
“We’re finding a little more traction in that midsize to SMB customer, more so than the larger enterprise, because we’re seeing that the enterprise generally would do it themselves with their own tools more often than an SMB or midsize customer does,” he says.
Solutions like those in the RECON family are a core part of Tech Data’s long-term strategy to keep pace with an industry transitioning from “second platform” server-client computing to “third platform” technologies like cloud computing and the Internet of Things.