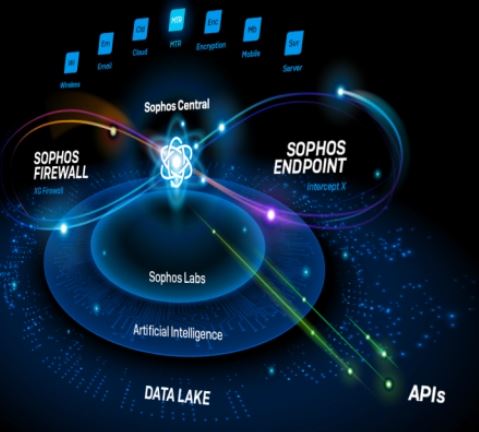
Sophos has introduced an extended detection and response (XDR) solution capable of collecting, analyzing, and acting on data from its own products and third-party platforms.
The system’s debut coincides with the official launch of a new ISV architecture from Sophos designed to let security vendors share telemetry from their products.
Due to ship on May 19th, Sophos XDR uses merged data from the company’s workstation and server protection solutions, email security software, and firewalls—including the next-generation firewall shipped two weeks ago—to identify and block sophisticated attacks that any one of those platforms might miss on its own. The solution will begin receiving input from Sophos Cloud Optix and Sophos Mobile as well later this year.
At the heart of the new solution is a custom-built, cloud-based data lake containing 30 days of cross-product information. Unlike other XDR offerings though, Sophos says, its system also draws on up to 90 days of information stored locally on protected endpoints, and provides access to real-time input as well.
“Say I’m in an investigation and I determine that a certain process is malicious. I can actually see what devices are currently running that process,” says Sophos Chief Product Officer Dan Schiappa.
The depth and breadth of Sophos XDR’s data set, he continues, result in better visibility into threat activity, and offer both security analysts and SIEM or SOAR platforms a rich pool of insights to mine for clues about current and emerging dangers.
Other features in the new product include the ability to schedule recurring queries in advance and to pivot from security queries to related sub-queries rapidly. “We’ll actually provide recommendations for a sub-query based upon a query you’re doing so you can get through nested queries very, very fast,” Schiappa says.
The system also comes with a library of pre-configured queries for less sophisticated users. Sources for those searches include the SophosLabs research unit, the Sophos Managed Threat Response security operations center, and the Sophos Artificial Intelligence team. Sophos adds queries to the catalog regularly in response to new threats, as it did recently to help organizations determine whether or not they were impacted by the Hafnium exploit.
At present, Sophos XDR users must at a minimum also have licensing for the Intercept X endpoint protection solution or Intercept X for Server.
Also announced today, and available now, is a refreshed edition of Sophos EDR, the vendor’s endpoint detection and response solution. New functionality in the update includes the scheduled query, query pivoting, and pre-written query features in Sophos XDR, as well as direct integration with the SophosLabs Intelix threat intelligence database.
“This now gives the operator the ability to dump a file or anything into the intelligence platform and get a really, really rich set of data back,” Schiappa explains.
The new cross-vendor architecture Sophos launched today, called the adaptive cybersecurity ecosystem (ACE), allows Sophos XDR to import and act on data from third-party security solutions. It also plays a broader, more ambitious role in Sophos’s strategic vision, however, by enabling other vendors to tie their products into the “synchronized security” technology that Sophos has long used to coordinate response activity across its own systems.
“We’re going to have APIs available for anywhere from just providing sensor information to the full spectrum of involvement,” Schiappa says. “It’s really kind of up to the vendors how they want to participate.”
In addition to contributing information, he adds, vendors will be free to extract data from the Sophos data lake for use in their own solutions.
Officially launching the ACE is a significant milestone both for Sophos and for Schiappa, who sketched out the concept behind the ecosystem with Sophos CTO Joe Levy on a napkin at an Oxford pub in 2017. Schiappa first shared the vision for ACE, then called “Project Darwin” inside the company, with ChannelPro the following year.
New research published by SophosLabs today illustrates why XDR was Gartner’s number one security and risk trend for 2020. The report describes a recent incident involving a large, unnamed North American business in which attackers compromised a Microsoft Exchange server and then utilized a variety of tools and techniques to steal account credentials, establish footholds on multiple endpoints, upload malware, and more at different times over a two-week period.
“There was no single point product that would have ever caught anything like that,” Schiappa observes.
Other security vendors, including Trend Micro in February and Fortinet in January, have rolled out or enhanced XDR products of their own.