 Is it too early to prepare for Post-Quantum Cryptography (PQC)?
Is it too early to prepare for Post-Quantum Cryptography (PQC)?
Absolutely not. PQC is already an emerging field. As Louis Cremen, an instructor from Australia, says, while it may take time to fully materialize, preparing now is crucial since the PQC era will arrive within a decade.
So, what is quantum computing?
Quantum computers perform calculations differently than our current devices, such as phones, watches, and computers, which rely on the “binary digit” or “bit.”
A bit has a binary "0 or 1" function, meaning it can be turned on or off.
Our devices use billions of bits in complex on/off combinations to deliver the services we expect.
Quantum computers, however, use quantum bits (qubits):
Qubits can store information in more sophisticated ways than bits.
They operate in a post-Einsteinian world of quantum physics, allowing them to exist in multiple states simultaneously (superposition).
Quantum computers create qubits by utilizing the quantum characteristics of particles such as ions, electrons, and photons, which provide far more computing possibilities than bits.
Notable milestones:
In 1994, Peter Shor's paper marked a significant quantum computing landmark.
IBM's Osprey, the world's largest quantum computer, uses the properties of ions to create 433 qubits.
Atom and other companies are achieving breakthroughs in quantum computing.
While it's still early for quantum computing, progress is significant and promising.
What are the security challenges of post-quantum computing?
The implications of practical qubit usage are astounding. Gartner predicts that by 2034, or even as early as 2029, practical post-quantum computers will be capable of breaking our current encryption algorithms.
Encryption vulnerability: The Advanced Encryption Standard (AES), a widely used symmetric key algorithm, could be easily decrypted within a decade.
Massive Data Risk: Data encrypted and stored under AES over the past twenty-five years could be decrypted, leading to significant data breaches.
Personal impact: Imagine your personal images and secret notes being decrypted years from now.
Organizational risk: The scale of data leakage could have major implications, including GDPR violations for European entities.
In a few short years, post-quantum computers will become more capable and accessible, posing significant security threats:
Store now, decrypt later: Collecting vast amounts of encrypted data to decrypt later using advanced quantum computing.
Machine learning: Developing AI models to defeat encryption. Employing sophisticated dictionary attacks through machine learning algorithms to quickly break encryption.
Preparing for PQC
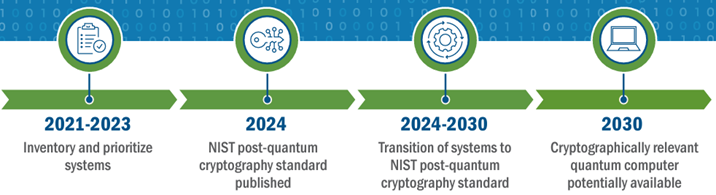
Although it's not doomsday yet, it's crucial to prepare for the impact of post-quantum computing. The National Institute of Standards and Technology (NIST), which developed AES, has introduced three post-quantum encryption standards. I had an enlightening conversation with NIST’s Bill Newhouse about his work in finalizing these standards. He also shared a helpful NIST infographic outlining steps organizations can take to get ready for a PQC world.

Preparing for a PQC world goes beyond adopting new encryption standards or using updated tech tools. The key is to mature your processes. According to the CompTIA State of Cybersecurity 2025 report, adopting a strategic approach to IT processes and creating imperatives around your organization’s architectures is crucial. This helps inventory critical data and prioritize systems.
First, identify the different architectures that need attention and improvement.
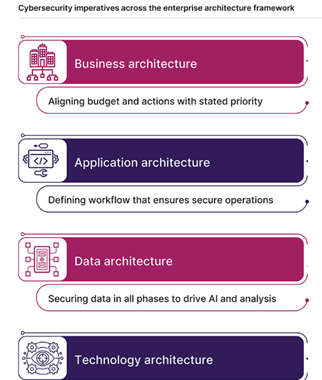
These architectures encompass Business, Application, Data, and Technology. The CompTIA report emphasizes that "Technology" should be addressed last. Simply upgrading VPN connections with new encryption isn't enough. As the world moves towards zero trust, traditional VPN technology becomes less critical. While upgrading your Secure Hash Algorithm (SHA) hash sizes can help, the true solution lies in creating policies and focusing on data processing across your organization. Workflow automation plays a key role in ensuring you can effectively upgrade encryption algorithms to protect users and data.
Following this approach will help implement the timeline suggested by NIST.
Practical ways to resist to quantum computing decryption attacks
Once you have improved your processes, you can then take some practical measures to resist post-quantum computing attacks as they arise. Many of these methods are now outlined in CompTIA’s SecurityX education program (formerly known as CASP+). The subject matter experts that have helped update SecurityX have kept current about how to prepare for post-quantum computing, as well as uses of AI. Stop-gap measures include:
Using Elliptical Curve Cryptography (ECC) with a sufficiently large key size, can help make your encryption a bit more resistant to PQC. This is likely the weakest option, but stronger than traditional RSA algorithms, but as you can see in the image below, it’s available right now.
Forward secrecy: In Transport Layer Security (TLS), the use of disposable, unique session keys to create the encrypted session. This technique protects previous encryption sessions against store-now, decrypt later attacks.
Key stretching: The use of multiple rounds of hashing to strengthen keys. Libraries such as bcrypt make it possible to add multiple hashes designed to slow down the hashing process, making it more difficult for attackers to conduct password cracking attacks.
Key splitting: Breaking a cryptographic key into multiple components. This way, if one element is seized and processed by a PQC process, the remaining elements remain encrypted.
Homomorphic encryption: Where data is converted into ciphertext, but the resulting ciphertext can still be used by the computers of other individuals, cloud providers, partner companies without being decrypted. The ability to perform mathematical calculations on encrypted data without first decrypting it has significant implications for privacy, as well as for strengthening encryption for PQC.
Envelope encryption: The use of a root key as a manager, or “wrapper” of multiple data encryption keys. Think of it as a mini Public Key Infrastructure (PKI) environment that adopts the strengths of symmetric and asymmetric key encryption, but also makes it easier to manage these keys.
None of these measures are "one-and-done" solutions; we no longer live in a binary world. SecurityX experts emphasize the need for workflow automation as a long-term strategy. However, these steps can still help manage security as we transition into a post-quantum computing world.
Blog Contribution by James Stanger, Chief Technology Evangelist

