Today’s managed IT service providers need a power management solution for their small and midsize business customers that not only protects against unplanned power outages but also lowers the risk of a supply chain cyberattack. That’s why Eaton’s power management solutions for distributed IT are built on four pillars: monitoring, management, automation, and cybersecurity.
 “Cybersecurity is a big part of that foundation,” says James Martin, global network connectivity product manager for Eaton. “Cybersecurity is a huge threat to business continuity. Ransomware attacks are on the rise. So we’re not only protecting businesses from loss of utility power, but from denial-of-service attacks and ransomware attacks.”
“Cybersecurity is a big part of that foundation,” says James Martin, global network connectivity product manager for Eaton. “Cybersecurity is a huge threat to business continuity. Ransomware attacks are on the rise. So we’re not only protecting businesses from loss of utility power, but from denial-of-service attacks and ransomware attacks.”
With Intelligent Power Manager (IPM) software that is part of the Brightlayer Data Centers suite from Eaton, MSPs can remotely monitor, manage, and control uninterruptible power supplies (UPSs) and other power devices on their customers’ networks. In addition, they can automate remediation to strengthen business continuity by ensuring system uptime and data integrity. “Human error is one of the biggest contributors to being vulnerable to a cybersecurity attack, so if you automate and script the configuration of these devices, you can reduce those human errors and ensure that a secure configuration is applied uniformly across your environment on each network card,” Martin says.
Importantly, cybersecurity is at the core of Eaton’s “secure-by-design” philosophy, and it’s embedded in all products and platforms we bring to market.
WHY PARTNER WITH EATON
- Seamless integration with key IT vendors (Nutanix, HPE, and Dell EMC
- Network interface cybersecurity certifications: UL2900-1 and IEC 62443-4-2
- Access to resources to help you find and close opportunities
- Numerous revenue opportunities to add power management to your portfolio
- Award winning and profitable partner program
Eaton’s “secure-by-design” philosophy assures that our products meet rigorous cybersecurity and safety design and testing standards. Our cyber experts meet and exceed competencies recognized by international standards organizations. Our cybersecurity processes and secure development lifecycle are integrated into product development and guide our labs, procurement, and design teams as the foundation of innovation. And our customized testing procedures help ensure our products comply with industry cybersecurity standards.
“We work with the Eaton Cybersecurity Center of Excellence to make sure that from the very beginning we’re designing products with cybersecurity in mind,” Martin says.
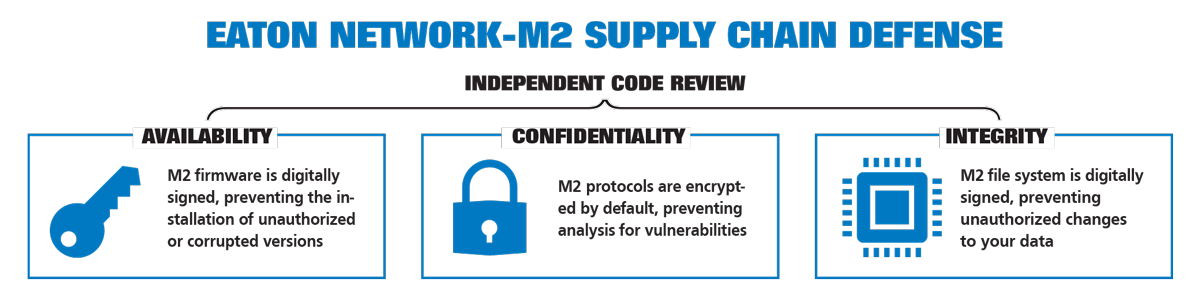
For example, Eaton’s Gigabit Network Card (NETWORK-M2) is the first product in the industry to receive both IEC (International Electrotechnical Commission) 62443-4-2 and UL 2900-1 certifications. As a result, this network card makes UPSs less vulnerable to cyberattacks.
Particularly in light of the TLStorm exploits earlier in the year that exposed more than 20 million UPSs to takeover, “people are taking a look at their power distribution devices such as UPSs and PDUs to make sure that a cyberattack is not going to bring down their business,” says Martin, who points out that not one Eaton UPS was impacted by TLStorm.
In addition, Eaton is proactive when it comes to helping its partners keep their customers safe, offering online resources, security briefings, and secure configuration documents. “It’s important that partners follow those secure configuration guidelines when they’re deploying our products, because if they use unencrypted protocols or enable connections or open up ports that are considered insecure, it will short-circuit the types of protections that we’ve put in place.”
With Eaton, security is never an afterthought—it’s part of our DNA, giving MSP partners the confidence that their SMB customers are better protected from unplanned business disruptions.