As predicted, on November 4, the United States Department of Defense (DoD) announced major changes to the Cybersecurity Maturity Model Certification (CMMC) program for defense contractors.
CMMC Model 2.0 is a more streamlined cybersecurity requirement and is designed to lower costs for smaller companies the DoD relies on to provide critical products and services used to defend the country. Most defense contractors will be allowed to self-assess their cybersecurity implementation instead of going through expensive certification assessments.
The new program:
- Lowers costs for smaller companies by drastically reducing the number of organizations that will need an expensive third-party certification
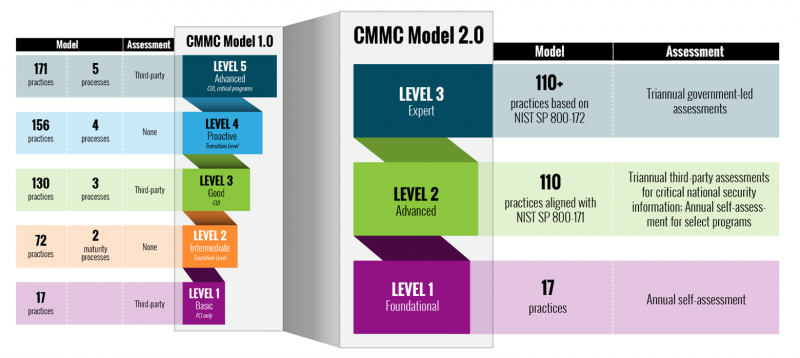
- Reduces the levels within the program from five to three (CMMC Model 1.0 Levels 2 and 4 have been eliminated)
- Allows companies at Level 1, and a subset of companies at Level 2, to self-assess
- Reduces the number of requirements in each level to align with current standards
- Makes earning certification easier by allowing companies to create timelines to address deficiencies instead of failing to earn certification by achieving a perfect score
- Allows certification requirements to be based on the sensitivity of information that flows down to subcontractors
- Increases the oversight of the assessment program
Program details, including the critical scoping guides required to create assessor training programs, will be released soon, according to the DoD. The current provisional assessment program has been suspended, and the announced changes indicate the CMMC implementation timeline may even be accelerated from the originally planned five-year rollout.
CMMC Levels and Requirements
Level 1 – Foundational. Includes the original 17 CMMC practices for contractors that do not process, store, or transmit Controlled Unclassified Information (CUI), but who do work with Federal Contract Information (FCI) that is not intended for public access. Contractors needing to comply with Level 1 will be allowed to self-assess and attest to their cybersecurity implementation. The DoD will utilize an audit program to validate compliance. Falsely attesting may result in False Claims Act lawsuits, which may be brought by whistleblowers working for defense contractors.
Level 2 – Advanced. Replaces the original CMMC Level 3 and is the minimum requirement for contractors that process, store, or transmit CUI. Level 2 now requires just the 110 practices defined in NIST Special Publication 800-171 and eliminates the 20 additional requirements in the original CMMC Level 3. Contractors will be required to pass a third-party assessment every three years, except for “select programs” (not yet defined) that will allow self-assessments. Previously, CMMC required a perfect score to earn certification. CMMC 2.0 allows companies “under certain limited circumstances” to create Plans of Actions & Milestones (POA&Ms) with strict timelines to achieve certification without a perfect score. Minimum scores will be required, and critical practices will be required to be completed and not addressed through POA&Ms.
Level 3 – Expert. Replaces the original CMMC Level 5 and will be required for contractors with extremely sensitive CUI. This level will require the 110 practices defined in NIST Special Publication 800-171 and selected (to be announced) practices in NIST Special Publication 800-172, down from the 171 practices in the original CMMC Level 5. Contractors will be required to pass a government assessment every three years.
 Source: US Department of Defense
Source: US Department of Defense
Increased Assessment Program Ethics Oversight
In my previous article, CMMC Growing Pains… or More?, I discussed the ethics claims against the CMMC Accreditation Body (CMMC-AB) and the resignations of multiple board members.
The DoD is taking a more active role by approving all CMMC-AB conflict-of-interest policies.
What Now???
CMMC is still a long way out.
The current requirement for a NIST 800-171 self-assessment still applies to all contractors that have the DFARS 252.204-7012 clause referenced in their contracts. This means that MSPs can continue to help their clients implement the 110 security practices in NIST 800-171.
The federal rulemaking process can take years. The CMMC-AB must achieve compliance with ISO/IEC 17011 to be able to certify assessors, which is why no one has yet been able to achieve full CMMC certification to conduct assessments.
Once CMMC’s new scoping guidance and timelines are announced, contractors will need to rely on information from the DoD or from their prime contractors about what level of compliance will apply to them. Because the new self-assessment process for Level 1 and limited contractors requiring Level 2 will include severe penalties for false attestations, MSPs should make sure their clients take the lower levels seriously.
CMMC 2.0 will be tied just to the NIST SP 800-171 and 800-172 documents, so the government will be able to make changes to those documents instead of going through a complete rulemaking process for separate CMMC requirements.
While MSPs were not specifically addressed in CMMC 2.0 or its frequently asked questions, I think it is likely that if any MSP system connects to a defense contractor’s network for remote monitoring and management, the MSP will need to be CMMC certified at the level of their clients. This means that if you have even one client that must be certified at CMMC Level 2 (the minimum if they process, store, or transmit CUI) then you will also need to be certified at Level 2, unless the DoD will consider MSPs part of the limited Level 2 group allowed to self-assess their implementation of NIST 800-171.
MIKE SEMEL is a former MSP and founder of Semel Consulting, which provides advisory services to MSPs and end users for compliance, cybersecurity, and business continuity planning. He worked with CompTIA to develop its Security Trustmark Plus, and with RapidFire Tools to create Compliance Manager GRC.














