Sophos has shipped a major upgrade of its endpoint detection and response (EDR) platform that adds threat hunting and remediation capabilities to enhanced versions of the product’s machine learning-based threat identification and malware analysis functionality.
“This is the most significant upgrade of any product we’ve ever had. It’s really that significant,” says Dan Schiappa, chief product officer at Sophos.
Available now at no extra cost as a component of both Sophos Intercept X Advanced for endpoints and Intercept X Advanced for Server with EDR, the new system offers protection for Windows, MacOS, and Linux devices. Sophos plans to add it to Cloud Optix, the cloud security solution it rolled out last year, before the end of the summer.
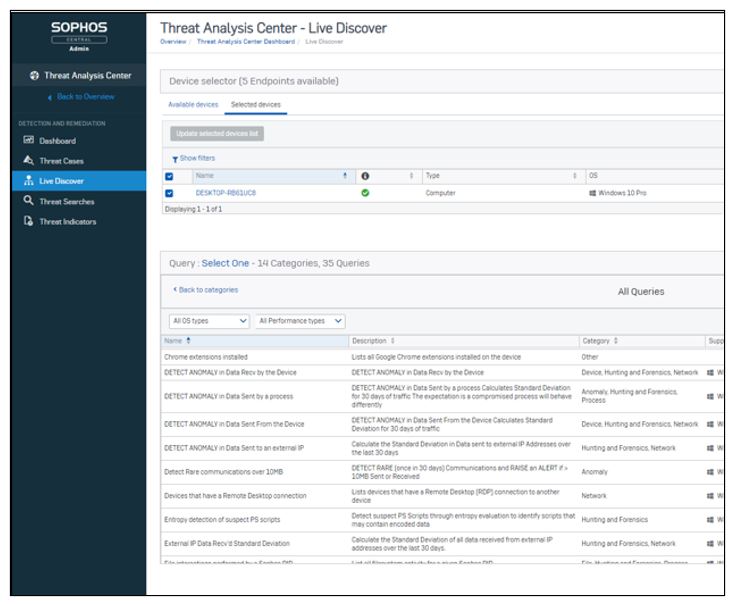
Users can employ the system’s new “Live Discover” threat hunting feature to query 90 days’ worth of data from thousands of endpoints and servers about issues like whether or not processes are trying to make a network connection on non-standard ports or which devices have unauthorized browser extensions.
“It’s all real-time data, and that’s super critical when you’re in detect mode,” Schiappa says.
The tool employs the familiar SQL language and automatically suggests how to complete a query as you compose it. “We show you as you’re writing it what the next command could be, very similar to what you might see in Excel when you’re doing an Excel formula,” Schiappa says, noting that the system comes with a library of pre-written queries as well.
Users can send a suspicious file identified during threat hunts to SophosLabs for deeper on-demand inspection. “We’ll do a machine learning scan on it, break it down for you, and give you some idea to help you decide whether it may be malicious or not,” Schiappa says. Companies can also pair the EDR solution with the Managed Threat Response service that Sophos introduced last October for assistance from live security experts.
Using the new system’s “Live Response” feature, technicians can mitigate threats found by Live Discover. Equipped with a command line interface and functionality normally found in RMM solutions, the tool lets administrators reboot devices, run scripts, terminate processes, install or remove applications, and more without switching to another application.
“You can actually jump on an endpoint or server and actually resolve the situation right from the console,” Schiappa notes.
The EDR solution’s mix of automated and hands-on capabilities is designed make it suitable for a wide range of users, he continues. “We’ve taken a tool that can be very powerful in the hands of a very sophisticated analyst and also made it very powerful for somebody who’s not sophisticated.”
Sophos’s latest solution arrives at a time of continuously escalating and increasingly dangerous threat activity. Sophos researchers describe one example of that phenomenon in a report published today about the Kingminer botnet, which utilizes brute force techniques to acquire server credentials and then spreads malware with help from a toolkit that includes the EternalBlue exploit, which gained worldwide notoriety three years ago in connection with the WannaCry ransomware attack.
Just over half of 5,000 global IT managers surveyed by Sophos recently—and 47% of those who work for businesses with 100-1000 employees—said their organization was struck by ransomware in the last year. Only 24% of businesses breached in those attacks detected the intrusion and blocked it before it encrypted their data. Figures like that, according to Schiappa, underscore the importance of utilizing both EDR software and behavior-based endpoint protection solutions like Intercept X.
“The ability and the necessity to be able to detect things in your environment has just become table stakes,” he says.
That users of the earlier EDR system get access to the updated product’s threat hunting and response features at no additional charge, he continues, is a compelling added bonus.
“It’s like you bought a Hyundai and you walked out your driveway one day and it’s a Mercedes,” Schiappa says. “Both are great cars. One’s a little more sophisticated than the other.”