White Papers - Page 5
Microsoft Education Partner Guide
Access this essential guide to learn about Microsoft education offerings through SYNNEX. Topics include the CSP advantage, student use benefits, the partner opportunity model, and resources for customers.
Simply complete the form below to download the full guide.
Build Recurring Revenue Streams and Sell More with SIPPIO
SIPPIO offers the only Azure-native, ready-for-consumption, globally available cloud solution that enables calling capabilities in Microsoft Teams. Delivered ‘as-a-service’ for customers through channel partners, integrators and managed service providers, SIPPIO’s per user, per month pricing model provides flexibility to scale with a choice of inclusive or consumption-based subscriptions.
Password Exposé: 8 Truths About Employee Passwords
Solving the password problem impacts security, productivity, and even employee satisfaction in the workplace. The organizations that can rapidly and effectively address that challenge are well-positioned to keep their business safe while building aninnovative workforce. Learn more from these eight truths about the threats and opportunities of employee passwords.
Simply complete the form below to download the full white paper.
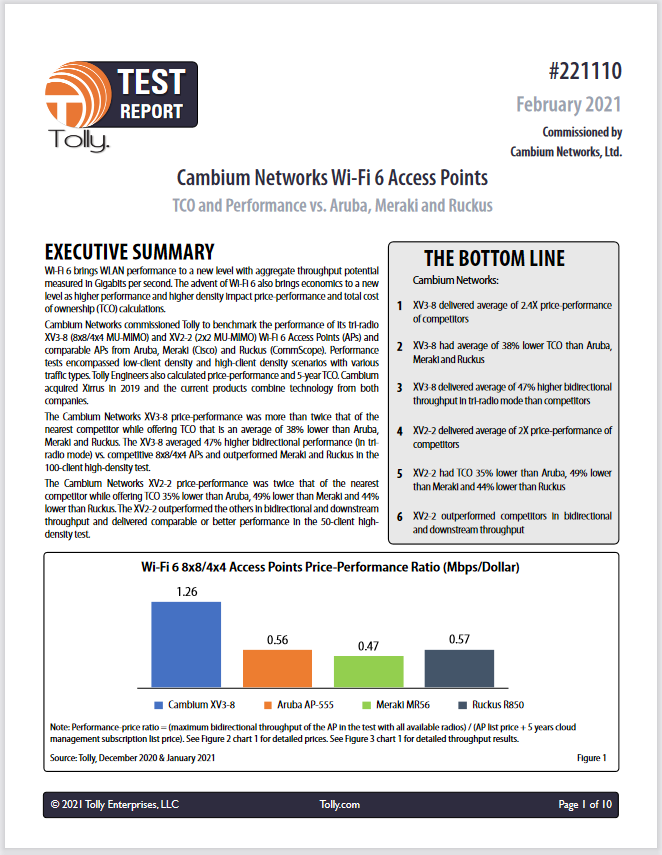
Cambium Networks Wi-Fi 6 Access Points Bringing Higher Performance and Economics
Wi-Fi 6 brings WLAN performance to a new level with aggregate throughput potential measured in Gigabits per second. The advent of Wi-Fi 6 also brings economics to a new level as higher performance and higher density impact price-performance and total cost of ownership (TCO) calculations. Get the full report that benchmarks the performance of its tri-radio XV3-8 (8×8/4×4 MU-MIMO) and XV2-2 (2×2 MU-MIMO) Wi-Fi 6 Access Points (APs) and comparable APs from Aruba, Meraki (Cisco) and Ruckus (CommScope).
The Hidden Costs of Ransomware
This eBook presents key findings from discussions with business leaders and IT professionals about how their organizations were affected by ransomware, beyond losing access to their data and paying a ransom. Download this resource today!
Profitability in the Cloud: Your Guide to Capturing New Markets
Grow your business with the right hybrid cloud distributor and give your customers a clear path to the cloud. Find out more on how SYNNEX provides deep expertise and personal support in almost every solution area a partner could want—and some of the highest margins in the channel.
Simply complete the form below to download the full white paper.
2021 Threat Report: Top Threats Now and Predictions for the Year to Come
In this report, we’ll break down a broad range of threat activity, offer insights into the trends we’ve observed, discuss wide-reaching impacts across industries, geographies, companies and people, and reveal what our threat experts expect to see in the coming year.
Simply complete the form below to download the full whitepaper.
The New ‘Cloud Normal’: Navigating the Post-COVID Cloud
This Expert Guide provides insight into the sales process for subscription-based everything, take a look at some of the top drivers for offering cloud-based managed services, explore why creating cloud solutions is far more profitable than reselling cloud products, and highlight some issues for navigating the post-COVID cloud, particularly around safety.
Simply complete the form below to read the full white paper.
Digital Remote Monitoring and Dispatch Services’ Impact on Edge Computing and Data Centers
Power and cooling infrastructure for edge com-puting and data center sites have roughly 3 times more data points / notifications todaythan it did 10 years ago. This paper explains how seven trends are re-defining remote monitoring and field ser-vice dispatch service requirements and how this will lead to improvements in operations and maintenanceof IT installations.
Simply complete the form below to read the full white paper.
A Quantitative Comparison of UPS Monitoring and Servicing Approaches Across Edge Environments
A fleet of single-phase UPSs distributed geographically across many edge sites presents unique challenges when it comes to monitoring and servicing. In this paper we present key considerations when deciding between managing the fleet of UPSs yourself vs. outsourcing that responsibility to a third-party vendor or partner.
Simply complete the form below to read the full white paper.