Topic: Security - Page 3
Cybersecurity in 2025: Critical Insights MSPs Can’t Afford to Miss from Channel Partners & MSP Summit in Las Vegas
Dive into the comprehensive cybersecurity content at the 2025 MSP Summit, tailored to tackle new challenges and threats.
Just Announced at ESET World 2025: Bold MSP-focused Products and Cybersecurity Enhancements
A quick look at the MSP-focused press releases that came from Day 1 of ESET World 2025.
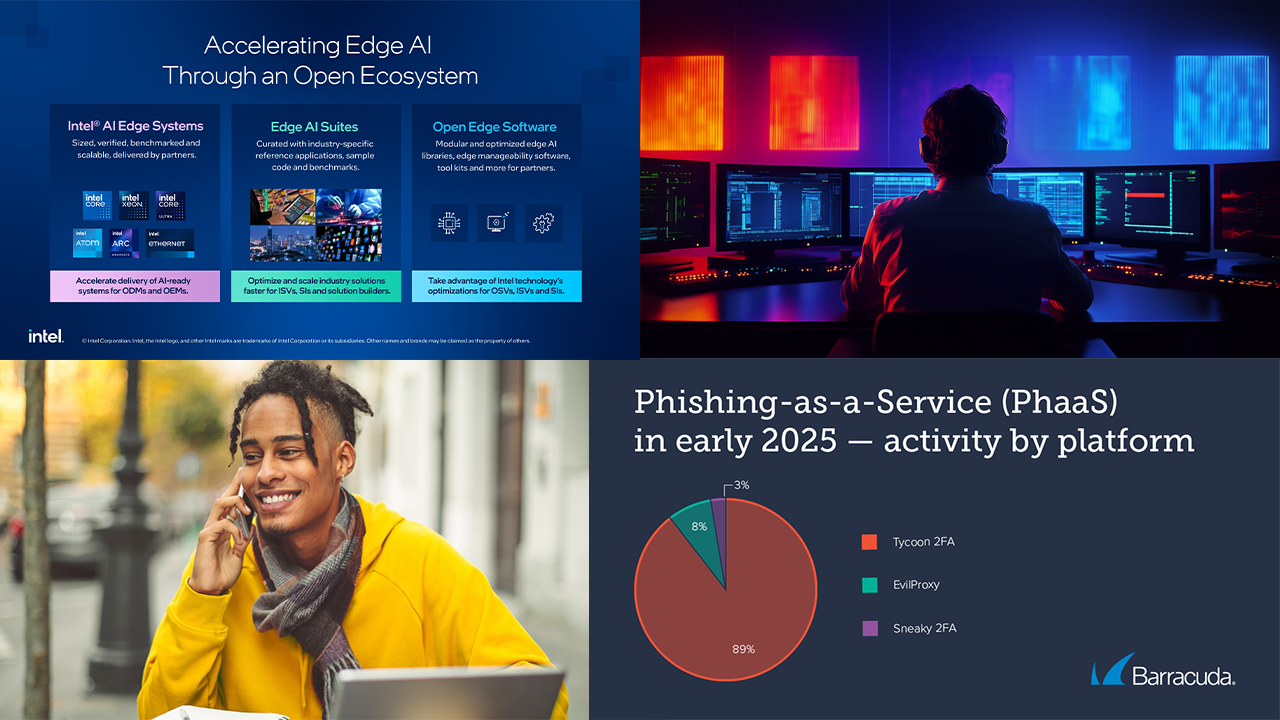
Key Channel Headlines: Intel Accelerates AI at the Edge Through an Open Ecosystem, N-able Extends Ecoverse Vision with Rewst and Cove Data Protection, and More
Stay informed with key details on the latest industry news, including announcements from Intel, N-able, Auvik, Hitachi, and more.
How to Boost Revenue and Defend Clients: Top Cybersecurity Insights for MSPs from ChannelPro Conference in Dallas
Enhance your cybersecurity services with key strategies and actionable advice from leading vendors Excel Micro, Choice Cyber Solutions, Calyptix Security, Octiga, and Cylerian.
Key Channel Headlines: Splashtop Adds Endpoint Management, Intel Expands Tiber Trust Services Portfolio, SUSE Announces Cloud Elevate for MSPs, and More
Intel announces important updates in the industry, along with Splashtop, Kaseya, ConnectWise, NinjaOne and more.
AI-powered Cybersecurity Won’t Save You: Why Human Error Is the Biggest Threat
Fighting AI with AI will not limit human error. Understand the importance of AI-powered tools in enhancing cyber resilience and combating challenges.
How Can MSPs Combat Cybercrime? Insights from Dallas’ Best MSP-focused Event
ChannelPro DEFEND shows that Texas MSPs are leading the way to combat AI-driven cyberattacks and improve their profitability.
Noteworthy Kaseya Innovations in Q1: Autotask, IT Glue, and more
Kaseya kicked off 2025 with a wave of noteworthy changes to its solution set. For MSPs, these updates mean greater efficiency, stronger defenses, and a fully integrated IT management experience.
Dropsuite and HaloPSA Unify Backup and Automation to Maximize MSP Efficiency and Profitability
Strategic Integration Automates Backup Oversight and Eliminates Revenue Leakage for Managed Service Providers
Key Channel Headlines: SonicWall Introduces SonicSentry MXDR, Wildix Expands Executive Team, and More
SonicWall Introduces SonicSentry MXDR, Wildix Expands Executive Team, >Dynabook Unveils Premium Copilot+PC Laptop, Enterprise Value Partners Launches to Redefine M&A Integration Success, and more.