On February 26, 2024, the U.S. National Institute of Standards and Technology (NIST) released the first major update to its Framework for Improving Critical Infrastructure Cybersecurity and MSPs should take note.
The original framework’s name reflected NIST’s goal to protect businesses in 16 designated critical infrastructure categories. The new framework known simply as the Cybersecurity Framework (CSF) 2.0 removes the critical infrastructure reference and has been designed to help secure all businesses.
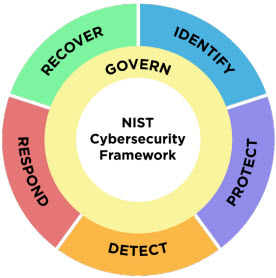
NIST CSF Version 2.0 adds “Govern” to its well-known Identify-Protect-Detect-Respond-Recover core functions. Unlike the original standalone core functions, Govern touches every other function and includes extensive supply chain flow-down requirements. Governance – corporate needs and policies, regulations, and legal requirements – must be considered when implementing each category and subcategory (control) throughout the new framework.
Many items from the retired NIST CSF version 1.1 have been shifted into the new Govern function.

Mike Semel
When NIST conducted its online workshop to talk about the first draft of CSF 2.0, over 7,000 people signed up from over 100 countries. Over a two-year period, public and industry workshops were conducted, comments were solicited, and drafts released to ensure that stakeholders had input as NIST designed the new framework.
The original NIST CSF has been called a landmark because it was translated into 12 languages and has been adopted by many countries across the world. The framework simplified cybersecurity and made it understandable to nontechnical business leaders by using commonly understood language. It has proven to be achievable because it allows flexibility when implementing cybersecurity by organizations of different sizes in different industries and different countries.
Even though the U.S. government does not require implementing the CSF, regulations and certifications – including HIPAA, PCI, SOC-2, and NY DFS Part 500 – refer to it to achieve compliance or offer benefits for it being the basis of a cybersecurity program. In four states, evidence of its implementation can be used to remove legal liability in lawsuits after cybersecurity incidents.
Guides and Tools
NIST CSF 2.0 is available as a pdf and a spreadsheet (automatic download). NIST also released multiple guides and tools to support implementation of CSF 2.0.
- A simple Resource Guide provides an overview.
- A Small Business Quick-Start Guide includes guidance that small organizations can understand when implementing a cybersecurity program.
- An Enterprise Risk Management Guide is specific to large enterprise companies.
- An Organizational Profiles Quick-Start Guide helps organizations identify their current state against their target state, resulting in a gap analysis.
- A Cybersecurity Supply Chain Risk Management (C-SCRM) Quick-Start Guide includes tips on risks associated with technology vendors and suppliers and is adaptable to businesses of all sizes and in different industries.
- A CSF Tiers Quick-Start Guide helps businesses classify the maturity of their cyber risk management program.
- A Community Profile guide helps industry organizations create templates for their stakeholders to implement cybersecurity programs.
To make NIST CSF 2.0 adoption easier, NIST simplified its original framework document format by removing the references to other standards, which have been moved to an online tool. This streamlined the original framework document format and eliminated the confusion caused when reference documents and frameworks changed from what NIST originally printed. Now, reference information for each CSF 2.0 subcategory can be kept current by NIST updating the online database whenever a reference framework or guide changes.
Why You Should Implement the NIST CSF
The NIST CSF has been proven over its 10-year history to be achievable and affordable by businesses of different types, sizes, industries, and countries. It has been adopted by other countries, including Canada, France, Uruguay, Saudi Arabia, and Israel. Guidance has been created for different categories of businesses, making the implementation tasks more understandable, more measurable, and easier to communicate to business leaders who do not have cybersecurity expertise.
Because the NIST CSF is a U.S. government standard recognized by multiple countries around the world, being able to prove you have consistently implemented it over time can give a high level of protection against regulatory audits and penalties, and a valuable defense in lawsuits.
As a HIPAA Recognized Security Practice – unlike nongovernmental cybersecurity frameworks including the CIS Controls – healthcare HIPAA-covered entities and business associates that can prove they have implemented the NIST CSF for 12 months prior to an audit or incident investigation can receive relief from audits and penalties. This is a valuable benefit considering the federal government has announced upcoming HIPAA changes, more audits, and increased penalties.
Consistent implementation of the NIST CSF 2.0 can help businesses adhere to regulations and to contractual and cyber insurance policy requirements.
Attorney Paul Greene of the HSE law firm recommends that his clients implement the NIST CSF over all other choices because as their attorney, he wants to be able to show a judge or jury during a lawsuit that his client has followed a U.S. government standard when building their cybersecurity program.
Impact on MSPs
MSPs will be affected in several ways. First, the CSF 2.0 framework’s new focus on governance and Cyber Supply Chain Risk Management will add scrutiny of MSPs by their clients. By implementing the CSF 2.0 for your services provider entity, and being able to prove it through documentation, you can lower your own risks, including having your errors and omissions (E&O) insurance fail to protect you.
Implementing the CSF 2.0 is a great way to prepare if you plan to have an independent CMMC Level 2 assessment so you can support defense contractor clients.
As an MSP, you can sell your clients a wide range of cybersecurity products and services, explaining each one and making each one a choice, or you can simply sell a client on the benefits of implementing the NIST Cybersecurity Framework and then show them how your entire stack of services aligns with their requirements. A single NIST CSF 2.0 sale to a client can eliminate the item-by-item buying decision and change how you explain the benefits you offer.
Implementing CSF 2.0 is also an opportunity for IT services providers to sell additional compliance services on top of your managed services. Creating the documentation to validate the CSF 2.0 implementation each month is a valuable service that clients will pay for once they understand the legal and regulatory benefits, and the risks they face without documentation that will be required for an audit, incident investigation, or lawsuit.
Each of these opportunities can add profit and bottom-line MSP company value to your investors and stakeholders.
Mike Semel, “The Complianceologist,” is president of Semel Consulting. He is a CMMC Certified Assessor, CMMC Certified Professional, CMMC Registered Practitioner, Certified Security Compliance Specialist, Certified HIPAA Security Professional, Certified Business Continuity Professional, and a Certified Cyber Resilience Professional.
Image: NIST